Customizing user access with Security Roles in Dynamics 365
When onboarding a new employee, the ability to quickly and efficiently provide permissions is paramount to that new employee settling in and jumping into the flow of work. Just as, if not more, important is taking access or abilities away if a position has shifted or an individual no longer works for the company to prevent over access and abuse of it.
Dynamics 365 applications have a variety of pre-built and editable security roles admin can assign to groups of employees, streamlining and enhancing security across the organization.
Security roles
Security roles in Dynamics 365 can be assigned by administration only, and they function by determining privileges that dictate what actions a user can and cannot perform for records and task-based items. For records, privileges include:
Create records in the entity
Read records in the entity
Write (update/change) records in the entity
Delete records in the entity
Append, or attach, this entity to other records
Append to, or attach other records, to this entity
Assign to other users on the entity
Share records with users/teams in the entity
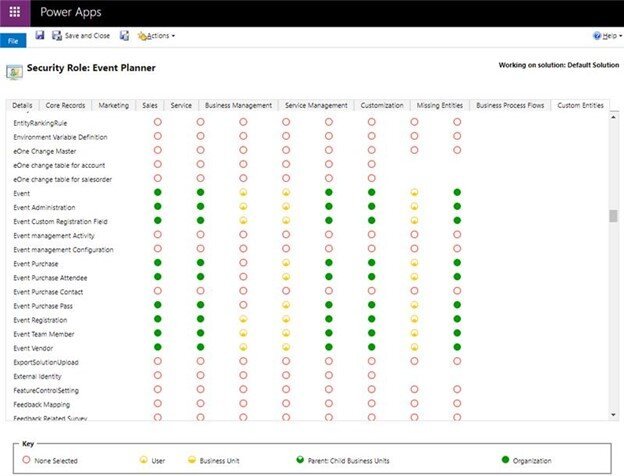
Privileges also define how broadly the privilege applies, ranging from no privilege at all to privilege across the entire organization. The access levels are color-coded circles, which are applied to each privilege:
The red outlined circle indicates no access to records.
The yellow quarter circle means a user has basic, or User, access to records a user owns and what is shared with them or the team.
The yellow half circle refers to local, or Business Unit, access to records throughout the user’s business unit.
The green three-quarter circle is deep, or Parent: Child Business Unit, access enabling users to manipulate records in the user’s business unit (called the parent business unit) and those subordinate to it (called child business units).
The green full circle is the global, or Organization, access level, which allows access to all records in an organization.
Task-based items (such as being able to bulk delete data or manage data encryption keys) include fewer permission levels and a simpler yes/no format of red and green circles, respectively.
When assigning and shifting security roles, record-based privileges are displayed at top and task-based privileges are listed in the Miscellaneous Privileges at the bottom of screen.
Business units
By default, Dynamics 365 creates a business unit that applies to the whole organization. Additional business units (called child business units) can be created if needed based on geography or function, such as departments or job roles.
To work within Dynamics 365 applications, a user must be part of at least one business unit and assigned at least one security role. If a user is assigned several roles in a business unit, the broadest permissions/privileges override roles with lesser permissions/privileges.
In addition, security roles are specific to the business units to which they are created. So, if a user moves from one business unit to another, they will lose all prior security roles and must be assigned roles in that unit.
Pre-built roles
Dynamics 365 provides many pre-built roles to jumpstart the business’ security right out of the box. These roles can be edited and saved anew, or used as is. Though admin can create a security role from scratch, it is far easier to edit the role closest to the permissions you are seeking. Security roles can be copied, saved as a new role, and edited to meet the specific needs of the company and the employee’s job responsibilities. This is an incredible boon to a business’ security, creating more exact, precise, and efficient control over employee access and abilities in Dynamics 365.
Some pre-built roles include those for Marketing Managers, Survey Designers, Sales Team Members, Forecast Managers, and Event Planners, to name a few.
Assigning, shifting, and revoking access and abilities within business applications can be time consuming if done manually and allows room for mistakes by granting too much or too little access. In each case, there are clear risks—too much access risks a user sees or manipulates data they should not, while too little can impact the employee’s ability to do their job. The pre-built security roles, available for use out of the box and editable for each company and employee’s unique needs, makes the daunting task of assigning permissions and a hill already climbed.